20 Dec pfSense Load Balancing multiple Surfshark’s WireGuard
pfSense Load Balancing multiple Surfshark’s WireGuard
Can pfSense be configured to load balance multiple Surfshark's WireGuard tunnels for increased throughput?
Overview
Requirements:
- Move multiple large files
- Ensure privacy and security
- Increase throughput
Challenges:
- Cutting-edge technology
- Limited documentation
- Limited experience/use cases
PoC – Test Environment:
- Internet uplink: Symmetrical 1 Gbps
- Netgate 1541 with Kernel mode WireGuard
- Surfshark, supporting the WireGuard VPN
- Load balancing multiple Surfshark VPN

Requirements
Our client required a privacy VPN connection to enhance security and privacy, with the objective of moving multiple large files as securely and quickly as possible, but wished to avoid the bandwidth restrictions typically experienced when using a single VPN tunnel.
Challenges
The challenge was that, while WireGuard was the best option for performance and simplicity, it was a relatively new technology and therefore not yet fully experienced or documented in specific use cases.
Proof of concept (PoC)
Our feasibility test involved using our test appliance, the Netgate 1541, equipped with pfSense Plus. The implementation of WireGuard within pfSense operates in Kernel mode, typically ensuring superior performance by handling VPN operations directly within the operating system’s kernel, thus enhancing speed and reducing latency.
The chosen privacy VPN was Surfshark, as it supports WireGuard. WireGuard and IPSec are currently the two best-performing VPNs, with WireGuard being incredibly simpler than IPSec and nearly as fast as hardware-accelerated IPSec.
The Internet uplink at the office was a symmetrical 1 Gbps.
Additionally, we aimed to test whether implementing multiple Surfshark-WireGuard connections in a load balancing configuration within pfSense would yield any performance benefits when copying multiple files simultaneously.
Implementation
Our test Netgate 1541 appliance was updated with the latest version of pfSense Plus, version 23.09.1. The full specifications of the appliance can be found here. WireGuard version 0.2.1 (pfSense-pkg-WireGuard-0.2.1) was configured within pfSense to establish a connection to the Surfshark privacy VPN. We set up multiple WireGuard connections to Surfshark, configured to operate in load balancing as described in the Netgate configuration documentation, available here.
Setting Up WireGuard Tunnels
- Create two distinct key pairs for the WireGuard tunnels.
- Configure the two WireGuard tunnels using the respective key pairs.
- Test the tunnels to ensure their functionality and connectivity.
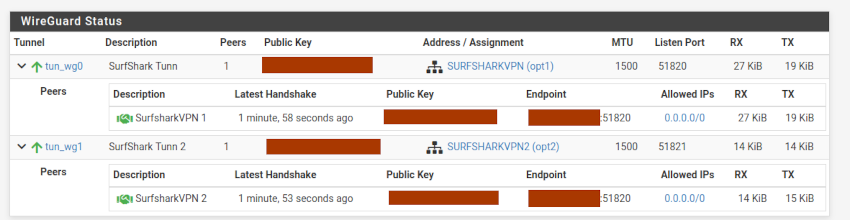
Assign Tunnels to pfSense Virtual Interface
Given that Surfshark assignes a /16 subnet for the peers configuration, the VPN interfaces were splitted into two /24 subnets, in order to prevent subnet overlap errors on the firewall.
For example, having a subnet of 10.14.0.0/16:
- Assign 10.14.0.2/24 for the first interface IPv4 address.
- Assign 10.14.1.2/24 for the second interface IPv4 address.
Creation of VPN Gateway
Create the VPN gateways used by the tunnel interfaces to forward the traffic to and assign them to the tunnel interfaces.
Configuring VPN Gateway Group
- Make a VPN gateway group that includes both configured VPN gateways.
- Assign both gateways to Tier 1 for load balancing functionality.
Setting Default Gateway
The options considered were to set up a Surfshark Gateway group as the default gateway and add a static route for Wiregurd to reach the Surfshark endpoints, or retaining the WAN internet connection as the Default Gateway and employing pfSense’s policy routing feature to direct LAN traffic to the Surfshark Gateway group.
We went for the LAN policy routing option.
Outbound NAT Configuration
Configure the outbound NAT rules to translate LAN traffic to Surfshark addresses, ensuring proper routing through the VPN gateways.
LAN Rule Setup
Create a LAN rule that allows incoming traffic and forwards it to the load balance VPN gateways for appropriate routing.
Testing
We utilised the Ookla speed test (www.speedtest.net), known for offering the option to use multiple simultaneous connections. This feature allowed us to use two Surfshark VPNs concurrently. Verification was achieved by adding two Traffic Graphs to the pfSense dashboard, one for each WireGuard interface. We observed that both interfaces were being utilised equally at the same time. A clip recorded during the speed test can be viewed for further insight.
Conclusions
The implementation of pfSense’s Load Balancing feature, in conjunction with Surfshark’s WireGuard tunnels on the Netgate 1541 appliance, has demonstrated the feasibility of load balancing integration. A single WireGuard VPN was almost capable of fully saturating the expected maximum speed of Surfshark’s WireGuard in the UK, anticipated to be between 760 and 950Mbps [Source: TechRadar]. Theoretically, a load-balanced connection using multiple Surfshark WireGuard tunnels should enable greater bandwidth for moving multiple large files securely and swiftly, aligning with our client’s requirements. While full verification of this capability was beyond the scope of our lab setup due to the symmetrical 1Gbps connection limit, the preliminary results are promising and suggest potential for higher bandwidth utilization when utilising a faster Internet uplink.
Lessons Learned
Selecting the appropriate Surfshark server is crucial to achieve optimal performance in the desired region. A critical phase in our test involved correctly setting up the routing to allow WireGuard to initiate its VPN connections to the Surfshark endpoints. It’s also important to consider the implications of running WireGuard in kernel mode versus user mode. Kernel mode offers superior performance, lower latency, and greater efficiency, while user mode, albeit slower and less efficient, provides better security isolation. Currently, there are no known security or vulnerability risks associated with running in kernel mode. However, our advice would be to consistently keep pfSense and WireGuard up to date. Maintaining system updates is a task with which we should all be familiar anyway.



